Cyber security: Attack of the health hackers

Roula Khalaf, Editor of the FT, selects her favourite stories in this weekly newsletter.
Last January an administrator at health insurer Anthem noticed an unusually complex query running on the computer network. It looked like a colleague was responsible, but a quick check revealed that it was coming from somewhere else.
Minutes later, Anthem was in crisis mode. Investigators believe the hackers were from China and had been operating undetected inside the company’s network for months. They gained access by tricking the employee to click on a phishing email that was disguised to look like an internal message.
Using the administrator’s credentials, hackers combed through Anthem’s database containing names, social security numbers and birth dates of over 78m people who have been enrolled in its insurance plans since 2004.
Anthem’s breach sent a wave of panic through the healthcare industry. It exposed clients’ most sensitive and valuable personal information, and revealed just how unprepared the health industry was to threats from increasingly sophisticated cyber criminals — and from nation states.
Hackers accessed over 100m health records — 100 times more than ever before — last year. Eight of the 10 largest hacks into any type of healthcare provider happened this year, according to the US Department of Health and Human Services.
Insurers scrambled to hire cyber security companies to scrub their systems. Premera Blue Cross, CareFirst BlueCross BlueShield, and Excellus Health Plan announced breaches affecting at least 22m individuals in total since March, including hacks that stretched back more than a year. Investigators told the FT that they believe some of the hacks are related and trace back to China.
The insurers face multiple investigations from state insurance regulators and attorneys-general and some could face fines for failing to comply with state data privacy laws, while federal law enforcement agencies are investigating who is behind the hacks.
“For a lot of them it is often less of a priority than it should be. Because their focus is often on many other things it creates a vulnerability that I think a lot of hackers have figured out,” said Deven McGraw, deputy director for health information privacy at the HHS’s Office of Civil Rights. “We’re seeing some pretty consistent areas of non-compliance across the board.”
The HHS is investigating the breaches and declined to comment on them specifically. Healthcare companies are required by privacy laws in numerous countries, including the US and UK, to protect personal data. Yet they have been inconsistent in maintaining basic security, say regulators.
In the UK, there have been no reported hacks at the National Health Service, but it has been fined £1.3m by the Information Commissioner’s Office, which conducts audits on behalf of the government over data privacy. The fines are mostly for sloppiness: lost laptops, files left at a grocery shop and records abandoned at a bus stop.
“The Health Service holds some of the most sensitive personal information available, but instead of leading the way in how it looks after that information, the NHS is one of the worst performers. This is a major cause for concern,” Christopher Graham, the Information Commissioner, said this year. ICO was granted new authority this year to conduct compulsory audits of NHS systems. “Protecting the security of data across government and especially within the health system is a top priority,” an NHS spokesman said.
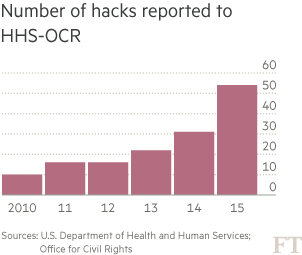
As in the UK, US healthcare providers see a majority of its data breaches falling into the categories of lost laptops or improper access to systems by insiders. Yet as more information is maintained in electronic form — an idea pushed heavily by the US government to make health records more portable — cyber intrusions have grown.
At some hospitals, the doctors who are often part of management have long resisted electronic measures that they thought could slow down or interfere with patient care. HHS’s Ms McGrath said this is a common excuse, but she said it is far more troubling that many companies don’t encrypt their data.
The problem has been exacerbated by the hundreds of hospital mergers that have occurred over the past few years, often resulting in multiple IT systems in one hospital group. Cyber security is often overlooked as a priority.
“It’s a very fragmented industry so there aren’t as many major players who drive the entire sector the way you’ve seen when it comes to financial services and cyber security,” said Bryan Palma, senior vice-president of Cisco’s Advanced Services in cyber security. “That is not happening in healthcare.”
With healthcare profit margins under pressure, only about 3 per cent of the IT budget is earmarked for cyber security, according to experts. Too many aspects of patient care are shared on a single hospital network. That means hackers in search of patient data could also disrupt life-saving equipment such as respirators running on the same network.
A new threat emerges
The threat changed this year with the emergence of hacks that investigators say are connected to China.
“We know of multiple threat groups operating out of China that have engaged in attacks in the healthcare industry,” said Charles Carmakal, an investigator with Mandiant, a cyber security company. Mandiant was hired by Anthem, Premera and others.
“While we believe we know from an organisational perspective who they are, we can’t tell who tasked them to do it. The big question is: are they hackers for hire and were they asked by the Chinese government to do this?” said Mr Carmakal.
The Chinese government has denied it was involved in the hacks. American investigators believe hackers in China targeted insurers in the US, including Anthem, to learn how medical coverage and insurer databases are set up, people familiar with the cases said. The records are also valuable for intelligence purposes. Addressing healthcare challenges has been a top priority of the Chinese government, which is facing an ageing and affluent population that is demanding better care.
“China is very interested in anything that will help them with the illnesses they are dealing with and changes in their population,” said Dmitri Alperovitch, co-founder of CrowdStrike, who declined to talk specifically about the Anthem breach. “For example, diabetes is a big problem in China so they have targeted companies in that space.”
China has promised to provide universal access to healthcare to all its citizens by 2020. Currently, China’s spending on healthcare per capita still lags far behind that of developed countries, and the healthcare system is riddled with corruption and kickbacks.
The industry is also an attractive target for criminals who sell personal health data on the black market. Medical records are much more valuable than credit card numbers because it often takes longer to detect so the data have a longer shelf life. Data such as social security numbers can be used in a range of schemes from tax refund fraud, insurance fraud or Medicare fraud.
A credit card record can be bought for about $1 on the black market, but “one person’s complete [medical] record I’ve seen anywhere between $200 and $2,000,” said Carl Leonard, an analyst for Raytheon Websense, a security company.
The market is flooded with stolen credit card details, he said, so “healthcare records attract the premium now”.
Investigators do not believe information from the Anthem breach has been sold on black markets. However, other hackers have targeted victims of the Anthem attack with fake emails that appear to be from Anthem or offer credit protection. Those emails aim to steal data that could be sold to criminals, people familiar with the case say.
Anthem plans to spend $130m over two years to better protect its networks from breaches. The company has assured regulators that it has strengthened its system, taking steps such as changing administrator passwords every 10 hours and hiring 55 cyber security experts.
Bad ‘cyber hygiene’
The hackers’ tactics vary but in many of the health breaches they set up domain names that look similar to the websites operated by the insurance companies, which were set up before the hacks were detected.
The fake sites often had one letter off from the authentic site or used the number “1” in place of where the letter “l” should be in site names, according to research done by cyber security companies ThreatConnect and Symantec.
For Anthem, which was formerly known as WellPoint, the domain www.we11point.com was set up. There was also prennera.com for Premera, EmpireB1ue.com for Empire Blue and caref1rst.com for CareFirst. All of these domain names were traced to China.
When the Anthem administrator discovered the hack on January 27 it was just as the hackers were extracting a large file of patient data. The hackers are believed to have been in the system for months, staying under the radar by running multiple queries against the database to understand it before they began removing files, a person familiar with the attack said.
The hackers used a repeating pattern of extracting data and slightly altering the query to avoid detection. They then removed the data and transferred it to an encrypted share site, similar to a drop box. The hackers chose a share site similar to one that Anthem already used, making detection tougher.
Anthem has been faulted for not having the right “cyber hygiene” or protections in place to minimise the risk of a hack or limit what information was vulnerable if the network was infiltrated.
Citing a report produced by Mandiant, a class-action lawsuit filed by dozens of Americans enrolled in its health insurance plans alleges Anthem did not implement a two-factor authentication, failed to require users to change their password and allowed employees to access personal information that went beyond the scope of their job.
Anthem also allegedly ignored alerts — including one that lasted a month, according to the lawsuit — and failed to implement systems that would monitor data usage or extractions. The company now has two-factor authentication for its high-level system administrators.
In a September 2013 audit of Anthem, the US Office of Personnel Management’s inspector general said the insurer had vulnerabilities that could provide a “gateway for malicious virus and hacking activity.”
Anthem could face fines and be required to take corrective measures.
Already, the hack has cost Anthem about $230m in legal and consultant fees. Most of the costs were covered by its cyber insurance policy. However, Thomas Zielinski, Anthem’s general counsel, told insurance regulators in August that its cyber insurance has become more expensive since the breach. Now Anthem is on the hook for the initial $25m cost of any breach, and has purchased a policy offering $100m in additional coverage.
“The [Anthem] breach has raised awareness,” Mr Palma said. “The healthcare industry is saying, ‘This is real now. There is precedent in our industry.’ They are late to the party but at least they are there now.”
Comments